Summary:
In order to further improve the accuracy and usability of the information system security risk assessment results and reduce the influence of subjective factors, the security risk of information systems is assessed based on the fuzzy analytic hierarchy process and the attack tree model. First, the attack tree model is used to describe the possible attacks of the system; secondly, it is assumed that each leaf node has different security attributes, and the fuzzy analytic hierarchy process is used to solve the weight of each security attribute. In order to reduce the influence of subjective factors on expert scores, each attribute is assumed The score is an interval variable, and an attribute probability occurrence model based on the interval variable is established. Finally, an example is used for analysis and verification, and the results show that the method not only further reduces the influence of subjective factors in risk assessment, but also has clear ideas, simple methods, and strong versatility and engineering application value.
â–
0 Preface
In the late 1990s, SCHNEIER B first proposed the concept of attack tree [1], which was later widely used in system security threat analysis and risk modeling [2-6] due to its clear hierarchy and intuitive image. However, in terms of quantitative analysis, traditional attack tree modeling has shortcomings, so a large number of improved methods of attack tree models have been proposed by industry scholars to improve the effect of network security risk assessment. Zhang Chunming et al. [7] proposed a network security event assessment method based on attack trees, which provided strong support for the formulation of security protection strategies. Wang Zuoguang et al. [8] carried out quantitative risk assessment of industrial control systems based on attack trees and CVSS, but did not analyze the attributes of each node when solving the probability of leaf nodes according to the CVSS 3.0 specification. Li Hui [9], Huang Huiping [10], Ren Dandan [11] and others used attack tree models to conduct threat modeling or security risk assessments on digital radio transmission security, industrial control systems, and vehicle self-organizing networks. There are still shortcomings in the calculation of security attributes. Based on the above literature, there are two main deficiencies when using the attack tree model to analyze system security risks: one is how to accurately analyze each security attribute; the other is how to quantitatively analyze the occurrence probability of each leaf node to reduce subjective factors Impact. In view of this, this article uses Fuzzy Analytic Hierarchy Process (FAHP) to improve the attack tree model. First, each leaf node is given specific security attributes, and then FAHP is used to calculate the weight of each security attribute based on the characteristics of the evaluation object At the same time, use the attribute probability occurrence model based on interval variables to solve the occurrence probability of each attribute, and finally calculate the occurrence probability of each leaf node. This model fully considers the game process of the offensive and defensive parties, can more accurately and reasonably evaluate the security risks of the system, and can provide technical support for the formulation of subsequent security protection strategies.
1 Attack tree model
In the attack tree model, the root node represents the attack target; the leaf nodes represent various attack methods used in the attack process [12-13]. The relationship between leaf nodes includes: AND (AND), OR (OR) and Sequence AND (Sequence AND, SAND) [7]. Use FAHP to improve the attack tree model and apply it to system security risk analysis. The main idea is shown in Figure 1.
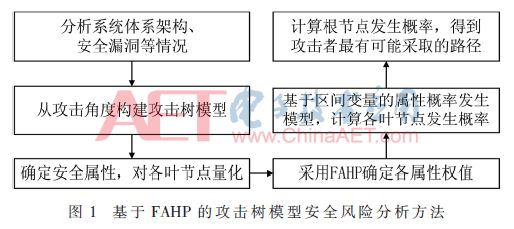
2 Improved attack tree model based on FAHP
2.1 Index quantification of leaf nodes
Since the realization of an attack may be affected by multiple factors, in order to reflect the influence of each factor on the attack event, three security attributes are assigned to each leaf node: the difficulty of realizing the attack (difficulty) and the cost of the attack required to realize the attack ( cost) and the probability of the attack being discovered (detection). According to the multi-attribute utility theory, the above three attributes are transformed into the utility value to achieve the goal, and the occurrence probability of the leaf node can be further calculated [8, 12]:


In practical engineering applications, the method of scoring by experts is usually used to assign values ​​to the security attribute values ​​of the leaf nodes. The following assumptions can be made before analysis:


2.2 Security attribute weight
FAHP is used to solve the weights Wdif, Wcos, and Wdet of the three security attributes of attack cost, difficulty degree and possibility of attack being discovered. Determine the relative importance of each factor at this level according to the relative degree of harm caused to the factors at the next level after the various factors of this level are attacked. This paper uses a scale of 0.1 to 0.9 to give a quantitative description of the relative importance. The comparison scale is shown in Table 2 [12]. Determine the importance of each attribute according to Table 2, and construct the judgment matrix C[15]:



a is inversely proportional to the difference of weights, that is, the larger a, the smaller the difference of weights; the smaller a, the greater the difference of weights. When a=(n-1)/2, the greater the degree of difference in weights. This paper takes a=(n-1)/2, RC is a third-order matrix, so a=(n-1)/2=1, where n is the order of the fuzzy consistent matrix, and we get wc=[0.383 4, 0.333 3, 0.283 3]. Therefore, Udif=0.383 4, Udet=0.333 3, Ucos=0.283 3 can be obtained, and the probability of occurrence of the leaf node is finally obtained by formula (1).
2.3 Probability of the root node
To calculate the occurrence probability of the root node, the attack path must first be determined. The attack path is an ordered set of a set of leaf nodes. The attack target can be achieved by completing this set of attack events (leaf nodes). The algorithm for constructing the attack path is as follows:
(1) Suppose G is the root node of the attack tree, and n is the degree of the root node.
(2) Analyze the possible attack path Ri=(X1, X2,..., Xm), i={1, 2,..., n}: search for all child nodes of G, if the child node is a leaf node Mi, determine one of the possible attack paths, otherwise, take each child node as the root and search for the next level child nodes until all possible attack paths are determined.
(3) Solving the probability of each attack path: using a bottom-up approach, the child node is used to solve the probability of the parent node. For details, please refer to literature [7] and literature [17].
Suppose there are n types of attack paths for a security event, and the attack path Ri=(X1, X2,..., Xm), i={1, 2,..., n}, where Xi represents each leaf node. Then the probability of occurrence of path Ri is: P(Ri)=P(X1)×P(X2)×…×P(Xm), i={1,2,…,n}, compare the calculation of the probability of occurrence of each attack path As a result, its numerical value can reflect the attacker's tendency to choose the attack method, and the attack method with the highest probability should be focused on.
3 Instance verification
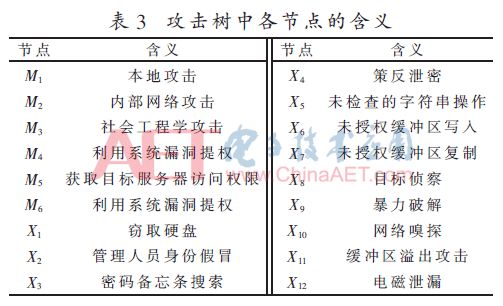
This article uses the literature [12] example for application verification analysis and comparison. Still taking the stealing of documents and data by internal personnel of a military business system as an example, the attack tree model is established, as shown in Figure 2, and the meaning of each node is shown in Table 3. The specific steps and typical insider attack methods can be referred to [12], which will not be repeated in this article.
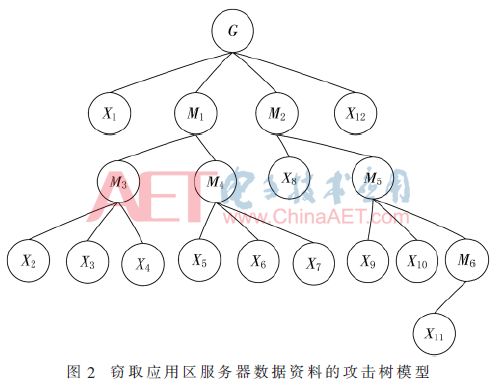
Using the scoring criteria in Table 1, score the security attribute value of each leaf node in the attack tree. In order to better verify the effectiveness of the method in this paper, the scoring results of the literature [12] are used here, as shown in Table 4.
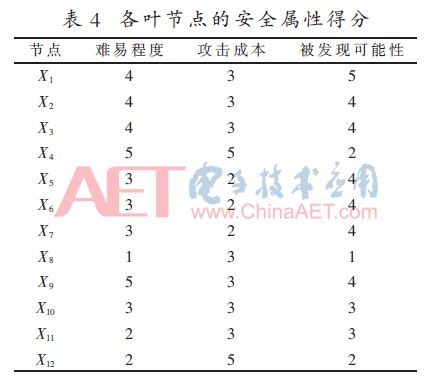
Assuming that the score of each leaf node in Table 4 is the median value of the score interval, and the value of X is the maximum value of the score level, 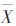
 mid+αXmid, X=Xmid-αXmid. Without loss of generality, taking the confidence level α=0.1, the interval value of each safety attribute score can be further obtained. According to formula (3) and formula (6), the utility value and corresponding weight of each attribute are respectively solved, and finally according to formula (1), the occurrence probability of each leaf node can be obtained, and the result is shown in Figure 3.
mid+αXmid, X=Xmid-αXmid. Without loss of generality, taking the confidence level α=0.1, the interval value of each safety attribute score can be further obtained. According to formula (3) and formula (6), the utility value and corresponding weight of each attribute are respectively solved, and finally according to formula (1), the occurrence probability of each leaf node can be obtained, and the result is shown in Figure 3.
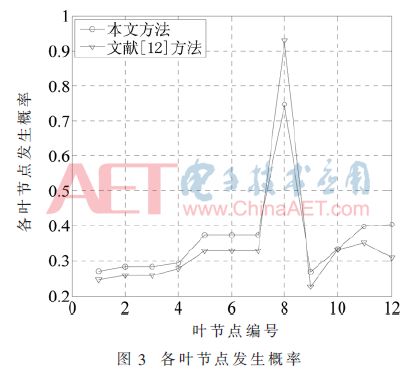
It can be seen from Figure 3 that the biggest difference between the method in this paper and the occurrence probability of each leaf node in the literature [12] lies in the occurrence probability of the leaf node X8, in this paper P8(X8)=0.746 9 and in the literature [12] P8(X8)=0.929 0. The main reason for this situation is that the weights of each security attribute are different. The weights of each attribute in the method and literature [12] are shown in Table 5.
When constructing the judgment matrix, the importance degree gradient of each attribute is small, and the weight value should be consistent with the importance degree. However, the value of each weight value in the literature [12] differs greatly. The fundamental reason lies in the subjectivity of the analytic hierarchy process. Stronger, and the fuzzy analytic hierarchy process is adopted in this paper, which reduces the influence of subjective factors to a certain extent, and further illustrates the effectiveness of the method in this paper.
According to the attack path algorithm in Section 2.3, list all possible attack sequences: R1=(X1); R2=(X2); R3=(X3); R4=(X4); R5=(X5); R6=( X6); R7=(X7); R8=(X8, X9); R9=(X8, X10); R10=(X8, X11); R11=(X12).
According to the formula P(Ri)=P(X1)×P(X2)×...×P(Xm), the probability of occurrence of each attack sequence is shown in Figure 4.
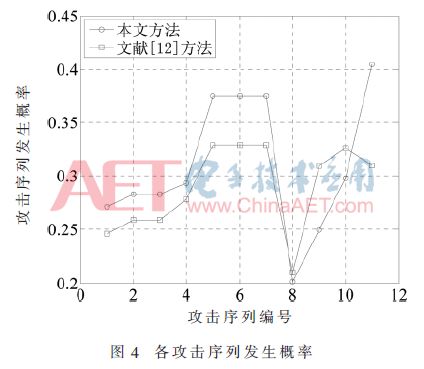
It can be seen from Figure 4 that R11 has the greatest probability of electromagnetic leakage, that is, an attacker is most likely to use electromagnetic leakage and other issues to attack; secondly, the attack tree model where insiders steal files has a greater probability of occurrence of R5, R6, and R7 attack sequences. , That is, an attacker is very likely to use the system's own loopholes to achieve secret theft. Compared with the conclusion of literature [12], the attack tree model has the highest probability of occurrence of R5, R6, and R7 attack sequences, followed by the probability of electromagnetic leakage. The fundamental reason for the error in the final conclusion is the different security attribute weights. The reason is the same as the occurrence probability of leaf nodes, so I won't repeat them here. Based on the above analysis, the military business system needs to take relevant security protection measures against the attack sequences R5, R6, R7, and R11.
The above analysis is the analysis conclusion given when the confidence level α=0.1. In order to further study the impact of different confidence levels on the security risk assessment results, the following gives the probability of occurrence of each attack sequence under different confidence levels, as shown in Table 6. .
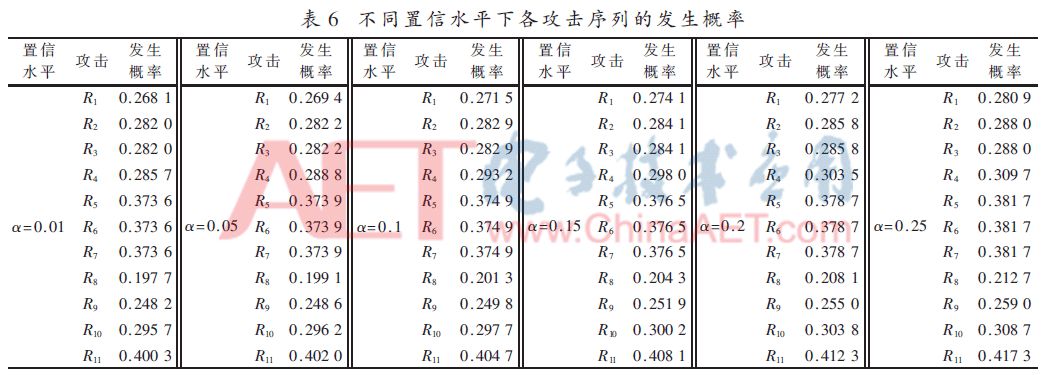
It can be seen from Table 6 that as the confidence level increases, the probability of occurrence of each attack sequence shows an increasing trend, which is mainly caused by the increase in the range of averaging the security attribute scores as the confidence level increases; with the confidence level The increase of, the order of the probability of occurrence of each attack sequence remains unchanged, which further shows that the value of the confidence level has less influence on the final consistency conclusion.
4 Conclusion
This paper proposes an information system security assessment method based on FAHP and attack tree, and compares and verifies it through examples. First, FAHP is used to solve the weight of each security attribute, which reduces the subjective factors in the evaluation process; secondly, when solving the probability of each leaf node, the score of each attribute is assumed to be an interval variable, which reduces the knowledge of experts to a certain extent. Determine the impact, further increase the amount of information of each attribute, and improve the accuracy of the occurrence probability of each leaf node; finally, the typical method steps for the security assessment of the information system are given through an example, and the most likely attacker is found The attack method adopted can provide technical support for the construction of the system's security protection system.
Hydrogel Film,Film Tpu Flexible Hd,Hydrogel Vs Glass,Tpu Film
Shenzhen TUOLI Electronic Technology Co., Ltd. , https://www.szhydrogelprotector.com