It is an ideal for each start-up company to turn from an unapproved “ugly duckling†to a “white swan†that is envied by everyone. Helping these start-ups solve security problems and achieve their dreams of better transformation is also the main service goal of the White Hat Andersen platform. Zhao Wu said, “Taking Andersen's name not only fits the difficulties of starting a business, but it is easy to remember because of the good intentions of the future.â€
The LOGO of Andersen's platform also used the image of a duckling. Â
 Zhao Wu, codenamed Zwell
Zhao Wu, codenamed Zwell
|Exploration and positioning
However, at the beginning of project conception, the service orientation of the platform was not so clear. The technical architecture in the platform is basically designed for large enterprises.
For example, big data technology, vulnerability monitoring technology, and workplace management traffic monitoring technology are common in the security protection of large enterprises such as BAT and 360, but they are not suitable for SMEs. The positioning of platform services is the Saas model. Large enterprises are more sensitive to public cloud services, and SMEs generally do not mind too much. Â
Large companies usually have about 200 security teams to support, and start-ups because of budget, experience, etc., resulting in poor security, but it is inevitable that attacks. Zhao Wu and his team finally decided to copy the security service model of large enterprises to SMEs, providing SMEs with a low-threshold, but effective solution to security problems in a certain way.
Although the entire project was planned for nearly a year, it took only three months from the start of the project to the completion of the demo. Â
Andersen’s full name is Andersen’s corporate threat perception platform. The SANS Institute defines threat intelligence as a set of data for security threats, threaters, exploits, malware, vulnerabilities, and hazard metrics, collected applications for evaluation. White Hat Lodge simply defines threat intelligence as:
Whoever wants to engage you, who gets you, and wants to do it, threatens intelligence that threatens corporate security. Â
Zhao Wu told Lei Fengwang (search for "Lei Feng Net" public concern) that companies are usually unfamiliar with their own assets. This will lead to the discovery of vulnerabilities and the repair efficiency is very low.
There was once a giant company that used a patch for three days because of insufficient knowledge of its own assets. Â
To timely and accurately find corporate security threat intelligence, Andersen’s platform will first sort out the company’s assets and put it on a fingerprint.
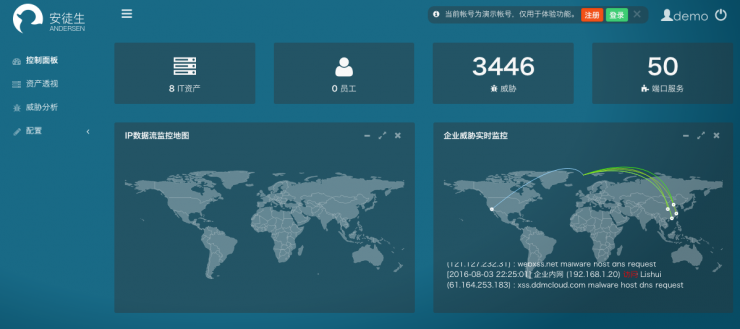 Andersen Platform Assets Perspective Page
Andersen Platform Assets Perspective Page
The Andersen platform divides corporate assets into two parts: IT assets and employee assets.
All machine-based devices in an enterprise are called IT assets. In addition to physical assets such as servers, notebooks, printers, and desktops, website operations also belong to IT assets that companies can manage.
Personnel assets are the information of employees or customers. For example, some employees will use the company's e-mail account to register accounts of other websites. Once other website service providers are invaded, the disclosure of corporate information will also pose a threat.
Fingerprint tags are the calibration of asset services.
Like people's fingerprints, IT assets also have fingerprints, just like device numbers. Some sources of vulnerability in enterprise security are ports or services where assets are open.
Where does big data come from?
Doing threat intelligence is inseparable from big data. Andersen obtains big data mainly through two channels, the Noesec big data security collaboration platform and the socialized threat intelligence gathering platform.
Prior to the development of the Andersen platform, White Hat established a Noesec big data security collaboration platform. The platform will automate all the fragmented corporate asset information publicly disclosed by the company. After accumulation and aggregation, the platform will form a huge asset system. Â
The black market underground trading centers in China are mainly forums and QQ groups. Andersen will obtain security threat information of service-related companies in a timely manner by launching white hats to monitor QQ groups and data forums. Zhao Wu introduced:
We will get the company’s data intelligence that is being trafficked from the white hat for the first time. We don’t know which data are leaked, but we also have a criterion for the information we obtain. We will use this data to communicate with the company. A communication that allows companies to identify themselves.
Baihathui also made a "Global Website Search" that targets only the Http protocol and Web application layer. By collecting global web service fingerprints, it is easy to identify which port a web site is on, which web server to use, which programming language, and which open source framework (eg, CMS, etc.). You can also find online Squid proxy servers around the world, which websites use Jquery, which online H3C routers, which websites use GeoTrust certificates, which websites have a specific Trojan horse, and which websites use CloudFlare's CDN.
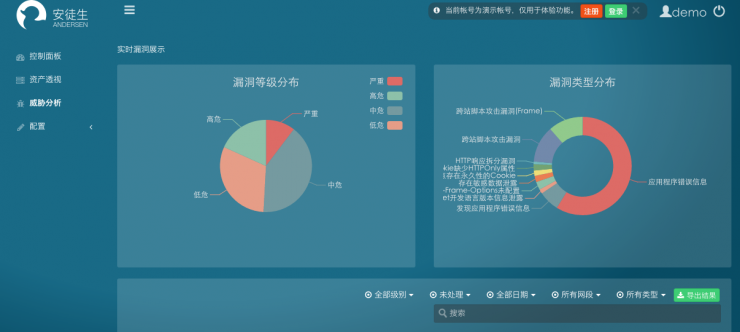 Andersen Platform Threat Analysis Page
Andersen Platform Threat Analysis Page
After obtaining the enterprise's threat intelligence information through big data, Andersen’s platform will analyze the intelligence, and classify the impact degree of the vulnerability and the difficulty of use into high-risk, medium-risk, and low-risk levels, and provide repair opinions for the company.
| The reality in fairy tales
At present, the demo of Andersen’s platform has gone online in the form of a website, and has been tested and polished in some familiar companies, and then adjusted and improved based on the opinions of the companies and industry insiders who are being tested. But Zhao Wu thinks
At present, the development progress of Baihathui's product development is still too slow. Although the technical team has expanded to 20 people and accumulated some product experience before, the pit can only be filled one by one.
The cloud service model requires powerful servers and bandwidth to support it. This is a huge cost.
As to when the Andersen platform began to spread out, Zhao Wu said he was not in a hurry.
On the one hand, the product has not yet reached a very good state. At this stage, as long as companies provide domain names, they can automatically monitor threat intelligence. But this is only external threat intelligence. It is probably a big hurdle to deploy some traffic-based enterprise probes to the interior. Whether the company will accept or accept it in any form requires discussion. Log analysis features have not yet been added, and machine learning features are still accumulating.
On the other hand, the promotion of the Andersen platform and the profit model are still being explored. Being recognized only does not mean that you are willing to spend on your product. Although profitability is not the ultimate goal, willingness to spend is an expression of product value recognition.
After working in the safety circle for many years, Zhao Wu also has his own experience in making products. The sooner he runs, the sooner he may die, and the small steps and jogging are all good things to do.
Customized Gift Bag From Stock,Direct Customized Gift Bags,Multi Style New Gift Bag,Cheap Opp Packaging Bag
Dongguan City Diadia Industry Co.,Ltd , https://www.diadiabag.com