In the industrial control network virus is getting more and more people's attention, the common virus sources of industrial control network include the system or industrial control software comes with a virus, download the third-party program carrying the virus, the user uses the U disk with the virus, because the industrial control network is relatively isolated, Therefore, mobile storage media such as U disk are more and more widely used, and it has become one of the main ways of spreading Trojans and viruses. There are many cases of virus transmission through U disk. The most well-known attack "Shenzhen" worm in industrial control system is to invade the control network through U disk, change the programs and data in PLC, and then cause serious damage to Iran's nuclear facilities. damage. This article will detail how the U disk virus spreads on the industrial control network and how to prevent it.
Second, the U disk virus transmission methodThe U disk virus is not a single virus, nor is it a virus that is transmitted only through a USB flash drive. It refers to all viruses that are transmitted through a USB flash drive. At present, there are mainly the following ways of U disk virus transmission:
1) Propagation through the autorun.inf file, the most common way of spreading this U disk virus;
2) Disguise as another file, the virus hides all the folders under the U disk, and copies itself into a file with the same folder name as the original folder name. When you click, the virus will execute itself and open the hidden one. Name folder;
3) Spreading through executable files is a traditional but very effective means of communication.
Third, U disk virus propagation prevention technology3.1 Traditional methods of prevention
Under normal circumstances, the basic security of the U disk virus can be achieved by modifying the security configuration of the operating system. At the same time, the professional virus software can be added to achieve the U disk virus prevention function. The operating system itself provides the following ways for U disk virus protection.
1) Turn off the automatic playback function, turn off the U disk autorun function of the windows system, and the U disk will not automatically run after being inserted into the computer to prevent anti-virus intrusion;
2) Modify the registry to make the U disk virus prohibit the automatic operation of the dual-drive letter;
3) When opening the USB flash drive, please select the right button to open. When using the USB flash drive, right click on the USB drive letter and select the "Open" command or enter through the "Explorer" window, because the double click actually activates the virus immediately. Doing to avoid poisoning;
4) Create an Autorun.inf folder. Create a folder named "Autorun.inf" on all disks. If there is a virus to invade, the virus cannot automatically create and create an Autorun.inf file with the same name. Even if you double-click the drive letter, the virus will not run. Thereby controlling the spread of the U disk virus;
3.2 Terminal protection software and security U disk combination
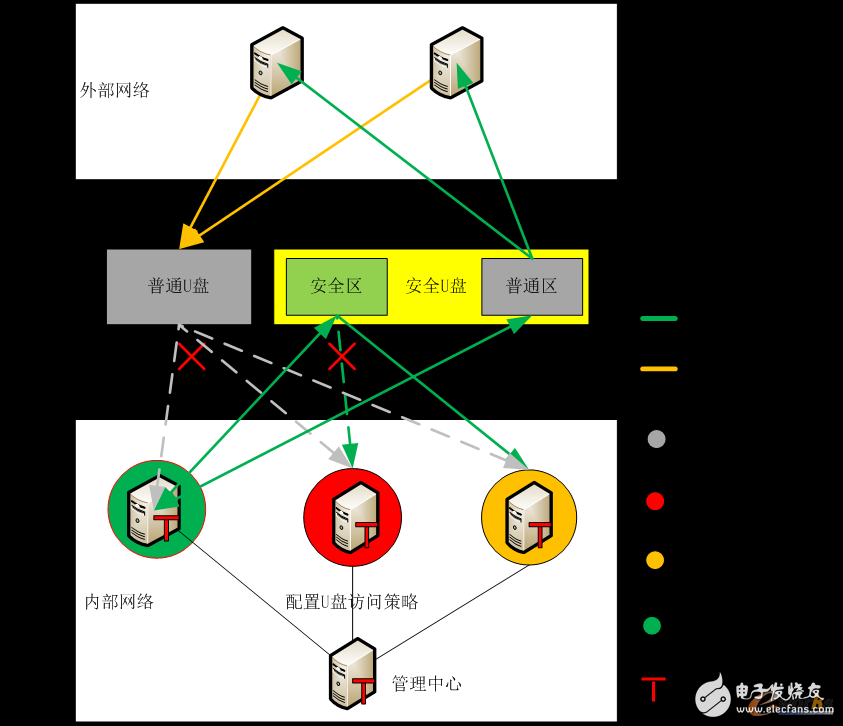
The management center is a centralized policy and log viewing center. The terminal protection software is installed on the internal network host by using the whitelisted terminal protection software. The management center can set the U disk access policy of the host (the access policy generally includes disable, read-only, read and write) and view the logs accessed by the U disk; the terminal protection software controls the read and write permissions of the ordinary U disk and the secure U disk connected to the host. Under normal circumstances, ordinary U disk is not allowed to be used by the host where the terminal protection software is installed. Restricting the security U disk can only be used in the machine where the terminal protection software is installed and the control host reads and writes the U disk according to the access policy, and records the U disk in real time. U disk violation access log.
1) For secure USB flash drives, the terminal protection software allows them to be used by default. The security U disk is divided into a normal partition and a secure partition, and different partitions are configured in different usage environments.
The security partition can be used only on the host where the IPC protection software product is installed. At the same time, the corresponding access policy can be opened and can be seen and used normally. At the same time, the security partition is encrypted, and a high-intensity secret algorithm is used to effectively prevent data leakage caused by brute force cracking. The security partition is mainly used to transmit data with high security level between the internal network and the internal network to ensure data security and ensure that data will not be leaked on the external network.
The normal partition can be read on the computer without the industrial control terminal protection software product, and the data can be written on the host where the industrial control terminal protection software is installed, which is mainly used for transmitting the data with lower security level;
2) For ordinary U disk, in order to protect the security of the internal network host, the ordinary U disk is not allowed to be used on the system where the terminal protection software is installed, so as to ensure that the protected host is not infected with the virus.
Dc Relay,Dc Power Relay,Condenser Contactor,Voltage Protection Relay
NanJing QUANNING electric Co.,Ltd , https://www.quanningtrading.com