DES is known as Data EncrypTIon Standard, a data encryption standard. It is a block algorithm that uses key encryption. It was identified by the US Federal Government's National Bureau of Standards as Federal Data Processing Standard (FIPS) in 1977 and authorized for non-secure government communications. Used in the process, and then the algorithm spread widely in the world. It should be noted that in some documents, DES as an algorithm is called Data EncrypTIon Algorithm (DEA) and has been distinguished from DES as a standard.
DES algorithmThere are three entry parameters of the DES algorithm: Key, Data, and Mode. Key is 7 bytes and 56 bits, which is the working key of DES algorithm; Data is 8 bytes and 64 bits, which is the data to be encrypted or decrypted; Mode is the working mode of DES, there are two kinds: encryption Or decrypt.
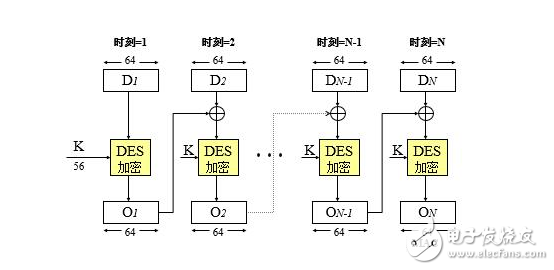
There are three entry parameters for the DES algorithm:
Key, Data, Mode
Key is a 64-bit key, Data is 64-bit data, and Mode is encryption or decryption.
The process of the DES algorithm:
1. Transform the entered key.
The user's 64-bit key, where 8, 8, 24, 32, 40, 48, 56, 64 bits are check digits, so that each key has an odd number of ones. So the key is actually 56 bits. The 56-bit key is transposed as shown in the following table.
57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 27, 19, 11, 3, 60, 52, 44, 36,
63, 55, 47, 39, 31, 23, 15, 7, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 28, 20, 12, 4,
The meaning of the table is the 57th shift to the 1st position, and the 49th shift to the 2nd position. . . . . . And so on. After the transformation, 56-bit data is obtained, which is divided into two parts, C[0][28], D[0][28].
2. Calculate 16 subkeys, and calculate C[i][28] D[i][28] to cycle left for the previous C[i-1][28], D[i-1][28] Move operation. The number of left shifts of 16 times is as follows:
1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16 (i)
1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1 (number of left shifts)
3. Calculate C[i][28] D[i][28] in series to get 56 bits, and then transform it to get 48-bit subkey K[i][48]
14, 17, 11, 24, 1, 5, 3, 28, 15, 6, 21, 10, 23, 19, 12, 4, 26, 8, 16, 7, 27, 20, 13, 2,
41, 52, 31, 37, 47, 55, 30, 40, 51, 45, 33, 48, 44, 49, 39, 56, 34, 53, 46, 42, 50, 36, 29, 32,
The meaning of the table is the 14th shift to the 1st position, the 17th shift to the 2nd position, and so on. During the process, it was found that the 9, 18, 22, 25, 35, 38, 43, 54 bits were discarded.
4. Transpose the 64-bit plaintext input. The transposition table is as follows:
58, 50, 12, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4,
62, 54, 46, 38, 30, 22, 14, 6, 64, 56, 48, 40, 32, 24, 16, 8,
57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3,
61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7
The meaning of the table is that when the first transformation, the 58th shift to the 1st position, the 50th shift to the 2nd position. . . . . . So on and so forth. The 64-bit data is obtained, and the data is divided into two blocks L[0][32], R[0][32].
5. Encryption process, transform R[i][32] into 48 digits, as follows, denoted as E(R[i][32])
32, 1, 2, 3, 4, 5,
4, 5, 6, 7, 8, 9,
8, 9, 10, 11, 12, 13,
12, 13, 14, 15, 16, 17,
16, 17, 18, 19, 20, 21,
20, 21, 22, 23, 24, 25,
24, 25, 26, 27, 28, 29,
28, 29, 30, 31, 32, 1,
6. X (E[R][32]) and K[i][48] are XORed to obtain 48 digits, and divide the 48 digits into 8 copies, 6 bits, B[8][ 6].
7. Replace B[i][6] with S[i]. The process is as follows: Take the first and sixth bits of B[i][6] and form a 2-digit m, m is the corresponding number of rows in S[i] (0-3), and take out B[i][ The 2nd to 5th digits of 6] are connected into a 4-digit n (0-15), n is the corresponding number of columns in S[i], and B[i] is replaced by S[i][m][n] [6]. S is a correspondence table of 4 rows and 16 columns, which is a 4-digit number, and a total of 8 Ss are defined as follows:
S[1]:
14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7,
0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8,
4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0,
15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13,
S[2]:
15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10,
3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5,
0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15,
13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9,
S[3]:
10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8,
13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1,
13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7,
1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12,
S[4]:
7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15,
13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9,
10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4,
3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14,
S[5]:
2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9,
14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6,
4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14,
11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3,
S[6]:
12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11,
10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8,
9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6,
4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13,
S[7]:
4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1,
13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6,
1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2,
6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12,
S[8]:
13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7,
1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2,
7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8,
2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11,
8. Connect the 8 4 digits obtained from B[i][6] through S to get 32 ​​digits. Transform this number as follows:
16,7,20,21,29,12,28,17, 1,15,23,26, 5,18,31,10,
2,8,24,14,32,27, 3, 9,19,13,30, 6,22,11, 4,25,
The obtained result is XORed with L[i][32], and the result is assigned to R[i][32].
9. Assign the value of R[i-1][32] to L[i] and cycle from 5. Until K[16][48] ends.
10. Combine the last L, R into 64 bits and then convert as follows to get the final result. This is an inverse change to step 4.
40, 8, 48, 16, 56, 24, 64, 32,
39, 7, 47, 15, 55, 23, 63, 31,
38, 6, 46, 14, 54, 22, 62, 30,
37, 5, 45, 13, 53, 21, 61, 29,
36, 4, 44, 12, 52, 20, 60, 28,
35, 3, 43, 11, 51, 19, 59, 27,
34, 2, 42, 10, 50, 18, 58, 26,
33, 1, 41, 9, 49, 17, 57, 25
The above is the encryption process of Des. The decryption process is the same. It only needs to reverse the order of 16 subkeys K[i][48].
Bitmain Miner:Bitmain Antminer L7 (9.5Gh),Bitmain Antminer L7 (9.16Gh),Bitmain Antminer L7 (9.05Gh),Bitmain Antminer L3+ (504Mh),Bitmain Antminer L3+ (600Mh),Bitmain Antminer L3++ (580Mh),Bitmain Antminer L3++ (596Mh)
Bitmain is the world's leading digital currency mining machine manufacturer. Its brand ANTMINER has maintained a long-term technological and market dominance in the industry, with customers covering more than 100 countries and regions. The company has subsidiaries in China, the United States, Singapore, Malaysia, Kazakhstan and other places.
Bitmain has a unique computing power efficiency ratio technology to provide the global blockchain network with outstanding computing power infrastructure and solutions. Since its establishment in 2013, ANTMINER BTC mining machine single computing power has increased by three orders of magnitude, while computing power efficiency ratio has decreased by two orders of magnitude. Bitmain's vision is to make the digital world a better place for mankind.
Bitmain Miner,antminer L3 Miner,Asic L3 Antminer,Bitmain Antminer L7,ltc miner
Shenzhen YLHM Technology Co., Ltd. , https://www.sggminer.com